Ethernet was developed
in the late 1970's by the Xerox Corporation at their Palo Alto
Research Centre in California. It has been estimated that over
70% of the worlds networks use the Ethernet protocol, so with
this in mind it would seem only sensible to discuss how it works.
If you would like to buy books on this subject, have a look at
the Network Cabling Help online book store.
OK, lets begin the lesson. Ethernet uses a protocol called CSMA/CD,
this stands for Carrier Sense, Multiple Access with Collision
Detection. To understand what this means lets separate the three
parts.
Carrier Sense - When a device connected to an Ethernet network wants to send data it first checks to make sure it has a carrier on which to send its data (usually a piece of copper cable connected to a hub or another machine).
Multiple Access - This means that all machines on the network are free to use the network whenever they like so long as no one else is transmitting.
Collision Detection -
A means of ensuring that when two machines start to transmit data
simultaneously, that the resultant corrupted data is discarded, and re-transmissions
are generated at differing time intervals.
Here are some animated GIF's
to help explain basic Ethernet operation, below each one is a description
of what is happening.
If you want to start an animation from the
beginning hit your browsers refresh button.

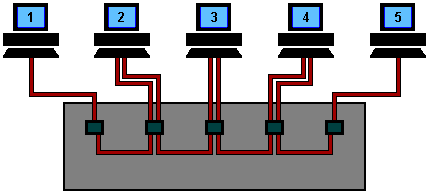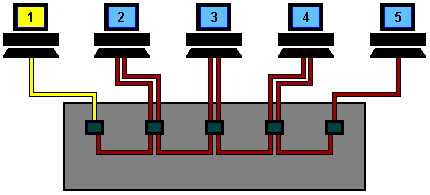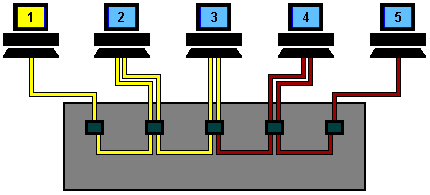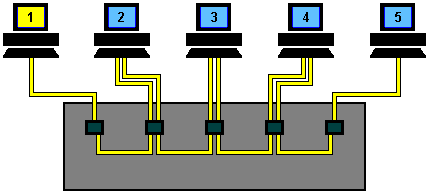
This is a coax based Ethernet network where all machines are daisy chained using RG58 coaxial cable (sometime referred to as Thin Ethernet or Thin-net).
Machine 2 wants to send a message to machine 4, but first it 'listens' to make sure no one else is using the network.
If it is all clear it starts to transmit its data on to the network (represented by the yellow flashing screens). Each packet of data contains the destination address, the senders address, and of course the data to be transmitted.
The signal moves down the cable and is received by every machine on the network but because it is only addressed to number 4, the other machines ignore it.
Machine 4 then sends a message back to number 2 acknowledging receipt of the data (represented by the purple flashing screens).
But what happens when two machines try to transmit at the same time? . . . . . a collision occurs, and each machine has to 'back off' for a random period of time before re-trying.
For the sake of simplicity I have omitted the acknowledgement transmissions from the rest of the animation's on this page.

This animation starts with machine 2 and machine 5 both trying to transmit simultaneously.
The resulting collision destroys both signals and each machine knows this has happened because they do not 'hear' their own transmission within a given period of time (this time period is the propagation delay and is equivalent to the time it takes for a signal to travel to the furthest part of the network and back again).
Both machines then wait for a random period of time before re-trying. On small networks this all happens so quickly that it is virtually unnoticeable, however, as more and more machines are added to a network the number of collisions rises dramatically and eventually results in slow network response. Time to buy a switch!!!
The exact number of machines that a single Ethernet segment can handle depends upon the applications being used, but it is generally considered that between 40 and 70 users are the limit before network speed is compromised.
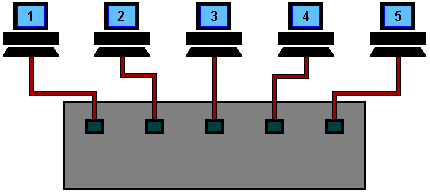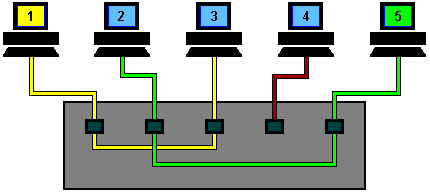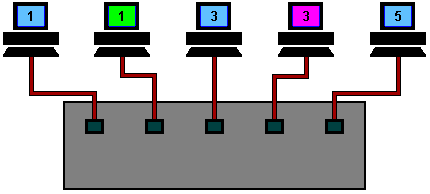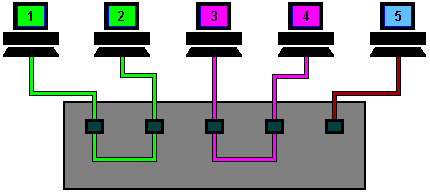
An Ethernet hub changes the topology from a 'bus' to a 'star wired bus', here's how it works.
Again, machine 1 is transmitting data to machine 4, but this time the signal travels in and out of the hub to each of the other machines.
As you can see, it is still possible for collisions to occur but hubs have the advantage of centralised wiring, and they can automatically bypass any ports that are disconnected or have a cabling fault. This makes the network much more fault tolerant than a coax based system where disconnecting a single connection will bring the whole network down.
To overcome the problem of collisions and other effects on network speed, a switch is used.
With a switch, machines can transmit simultaneously, in this case 1 & 5 first, and then 2 & 4. As you can see, the switch reads the destination addresses and 'switches' the signals directly to the recipients without broadcasting to all of the machines on the network.
This 'point to point' switching alleviates the problems associated with collisions and considerably improves network speed.
In the real world however, one or more of these machines will be servers, and as most network traffic is between the clients and a server a serious bottle neck can occur. The answer to this problem is to make server connections faster than the clients. The normal solution is to have the
client machines on 100Mbs ports and the servers on 1000Mbs ports (Gigabit Ethernet). This ten to one ratio is usually adequate because not all of the clients will need to access the servers at the same time.
Token Ring
Unlike Ethernet, Token Ring uses a ring topology whereby the data is sent from one machine to the next and so on around the ring until it ends up back where it started. It also uses a token passing protocol which means that a machine can only use the network when it has control of the Token, this ensures that there are no collisions because only one machine can use the network at any given time.
The
Basics
Here is an animated GIF that shows
the basic operation of a Token Ring, and below is an explanation
of what is going on.
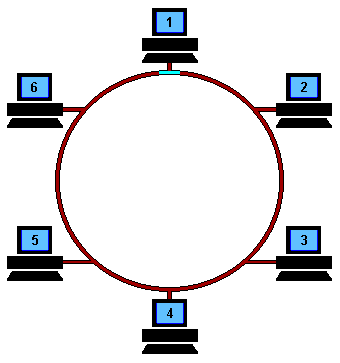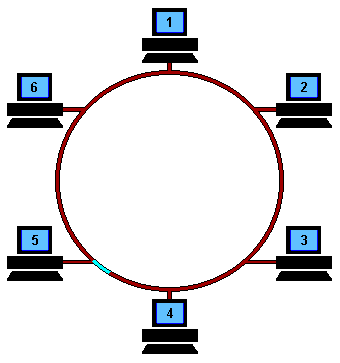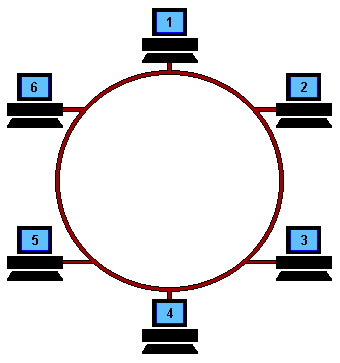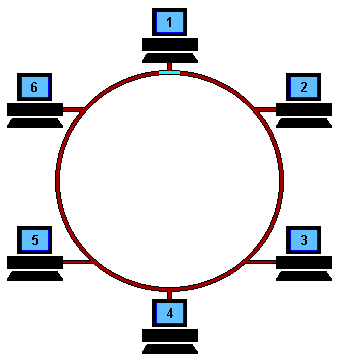
Hit 'Refresh' on your browser to start the animation from the beginning At the start, a free Token is circulating on the ring, this is a data frame which to all intents and purposes is an empty vessel for transporting data. To use the network, a machine first has to capture the free Token and replace the data with its own message.
In the example above, machine 1 wants to send some data to machine 4, so it first has to capture the free Token. It then writes its data and the recipient's address onto the Token (represented by the yellow flashing screen).
The packet of data is then sent to machine 2 who reads the address, realizes it is not its own, so passes it on to machine 3. Machine 3 does the same and passes the Token on to machine 4.
This time it is the correct address and so number 4 reads the message (represented by the yellow flashing screen). It cannot, however, release a free Token on to the ring, it must first send the message back to number 1 with an acknowledgement to say that it has received the data (represented by the purple flashing screen).
The receipt is then sent to machine 5 who checks the address, realizes that it is not its own and so forwards it on to the next machine in the ring, number 6.
Machine 6 does the same and forwards the data to number 1, who sent the original message.
Machine 1 recognizes the address, reads the acknowledgement from number 4 (represented by the purple flashing screen) and then releases the free Token back on to the ring ready for the next machine to use.
That's the basics of Token
Ring and it shows how data is sent, received and acknowledged, but Token
Ring also has a built in management and recovery system which makes it
very fault tolerant. Below is a brief outline of Token Ring's self maintenance
system.
Token
Ring Self Maintenance
When a Token Ring network starts up, the
machines all take part in a negotiation to decide who will control the
ring, or become the 'Active Monitor' to give it its proper title. This
is won by the machine with the highest MAC address who is participating
in the contention procedure, and all other machines become 'Standby Monitors'.
The job of the Active Monitor is to make sure that none of the machines are causing problems on the network, and to re-establish the ring after a break or an error has occurred. The Active Monitor performs Ring Polling every seven seconds and ring purges when there appears to be a problem. The ring polling allows all machines on the network to find out who is participating in the ring and to learn the address of their Nearest Active Upstream Neighbour (NAUN). Ring purges reset the ring after an interruption or loss of data is reported.
Each machine knows the address of its Nearest Active Upstream Neighbour. This is an important function in a Token Ring as it updates the information required to re-establish itself when machines enter or leave the ring.
When a machine enters the ring it performs a lobe test to verify that its own connection is working properly, if it passes, it sends a voltage to the hub which operates a relay to insert it into the ring.
If a problem occurs anywhere
on the ring, the machine that is immediately after the fault will cease
to receive signals. If this situation continues for a short period of
time it initiates a recovery procedure which assumes that its NAUN is
at fault, the outcome of this procedure either removes its neighbour from
the ring or it removes itself.
Token Ring Operation using a Hub
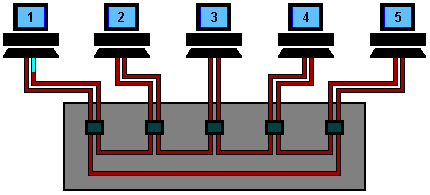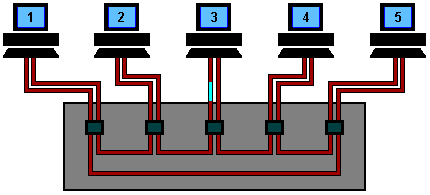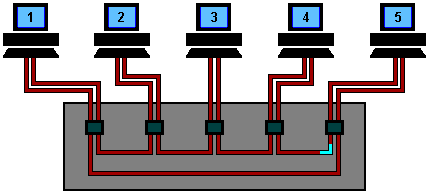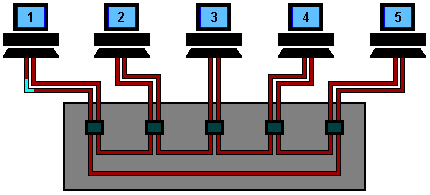
A Token Ring hub simply changes the topology from a physical ring to a star wired ring. The Token still circulates around the network and is still controlled in the same manner, however, using a hub or a switch greatly improves reliability because the hub can automatically bypass any ports that are disconnected or have a cabling fault.
Further advancements have been made in recent years with regard to Token Ring technology, such as early Token release and Token Ring switching but as this site is primarily concerned with cabling issues we will not go into any more detail here.